CVE-2025-55182 Exploitation Module Now Live in IRIS C2
A fully-featured exploitation module for the critical React Server Components vulnerability enabling unauthenticated Remote Code Execution.
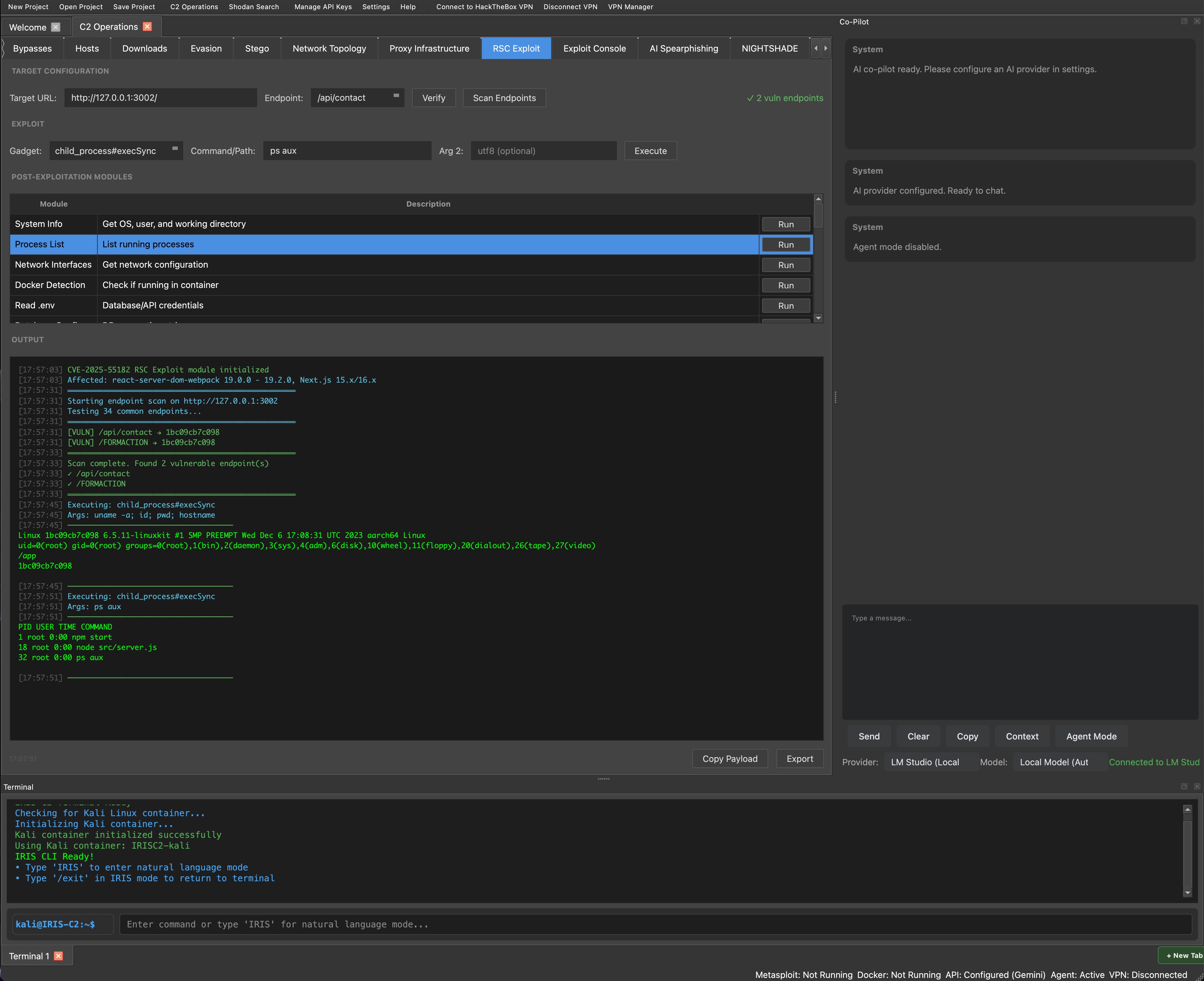
The IRIS C2 RSC Exploit module provides a complete workflow for exploiting CVE-2025-55182 in vulnerable React Server Components deployments.
Overview
We're pleased to announce the integration of a fully-featured CVE-2025-55182 exploitation module into IRIS C2. This critical vulnerability affects React Server Components in react-server-dom-webpack versions 19.0.0 through 19.2.0, as well as Next.js 15.x and 16.x applications utilizing the App Router with Server Actions. The vulnerability enables unauthenticated Remote Code Execution through a flaw in how the framework processes incoming form data.
How The Vulnerability Works
React Server Components introduced a feature called Server Actions, which allows server-side functions to be invoked directly from client-side forms. When a user submits a form, the RSC framework deserializes the incoming multipart form data to determine which server action to execute and with what arguments.
The vulnerability exists in the decodeAction() function, which processes a special form field that specifies which module and function should handle the request. Due to a missing hasOwnProperty check, an attacker can inject a crafted JSON payload that references arbitrary Node.js built-in modules rather than legitimate application code.
By specifying modules like child_process, fs, or os along with their exported functions, an attacker gains the ability to execute shell commands, read and write files, or perform other system-level operations on the server. The payload is delivered through a standard HTTP POST request with multipart form encoding, making it trivial to exploit and difficult to distinguish from legitimate form submissions without deep packet inspection.
IRIS C2 Module Capabilities
Target Configuration & Verification
The module provides a clean interface for specifying the target URL and endpoint. A one-click verification feature sends a silent probe using os#hostname to confirm RCE capability without generating suspicious log entries. The status indicator immediately reflects whether the target is vulnerable.
Automated Endpoint Discovery
Rather than manually guessing which endpoints accept Server Actions, operators can use the Scan Endpoints feature to automatically probe over 35 common React and Next.js API surfaces. The scanner tests endpoints like /api/contact, /api/submit, /api/auth/*, /FORMACTION, and many others. Vulnerable endpoints are highlighted in real-time and automatically added to the endpoint selector for immediate use.
Exploitation Gadgets
The module supports multiple Node.js module gadgets depending on operational requirements. Command execution through child_process#execSync provides direct shell access. File operations via fs#readFileSync and fs#writeFileSync enable data exfiltration and payload deployment. The os#hostname gadget offers a silent fingerprinting option with minimal forensic footprint.
Pre-Built Post-Exploitation Modules
The module ships with over 20 ready-to-use post-exploitation actions organized by operational phase.
Reconnaissance modules gather system information, enumerate running processes, map network interfaces, and detect containerized environments. These provide the situational awareness needed before deeper exploitation.
Credential harvesting modules target common secret storage locations including .env files, database configuration files, backup credential stores, bash history, and SSH keys. Many Node.js applications store sensitive credentials in plaintext configuration files, making this phase particularly fruitful.
Data exfiltration modules extract business-critical information such as customer records, order data, and internal network topology from hosts files and known_hosts entries.
Persistence options range from conservative to aggressive. Operators can choose between writing a webshell to disk, executing an in-memory backdoor that leaves no file artifacts, or establishing a reverse shell connection. The in-memory option binds a webshell to port 8888 without touching the filesystem, while the reverse shell option allows operators to specify their callback IP and port for a connect-back session.
Custom Payload Builder
For scenarios not covered by the pre-built modules, the custom payload interface allows selection of any supported gadget with arbitrary arguments. Operators can craft specific commands, target particular files, or chain operations as needed.
Operational Considerations
The module provides OPSEC guidance for each gadget type. File read operations and hostname queries generate minimal forensic evidence, while command execution creates process artifacts that may be logged or detected by EDR solutions. Persistence mechanisms vary in their detection risk—memory-only backdoors leave no disk artifacts but don't survive process restarts, while disk-based webshells persist across restarts but create discoverable files.
The export functionality captures the full session log for reporting, and the copy payload feature generates equivalent curl commands for use in other tooling or documentation.
Affected Versions
The vulnerability affects react-server-dom-webpack versions 19.0.0 through 19.2.0, with fixes available in 19.2.1 and later. Next.js applications using the App Router with Server Actions in versions 15.x and 16.x are affected when using vulnerable RSC packages.
Conclusion
The CVE-2025-55182 module provides IRIS C2 operators with a complete workflow for exploiting vulnerable React Server Components deployments. From automated endpoint discovery through credential harvesting and persistence establishment, the module delivers production-ready capabilities with appropriate OPSEC options for various operational contexts.
Update your IRIS C2 installation to access this module.
Want to Learn More?
Contact our team to schedule a demonstration or discuss how IRIS C2 can enhance your offensive security capabilities.
info@IRISC2.com